Control Technologies /
Techno Contrologies /
Nonelectric Hog Stool /
Electronic Ghost Loon /
No Troll Techno Cogies /
Coercing Lens Hot Loot /
Echelon Scorn Logo Tit
Raumkontrolle & die künstlerische Umwidmung von Kontrolltechnologien
Workshop für interessierte Studierende & Teilnehmer des Surveillant Architectures Seminars
23. & 24. 1. 2013, 10-18h
room 2, Filzengraben 2a
Im ersten Teil des Workshops lernen wir, wie man Unzulänglichkeiten und kleine Fehler in Schlössern ausnutzt, um diese gewaltfrei zu öffnen. Das “Türöffnen ohne Schlüssel” wird international als Sport betrieben. Der deutsche Meister von 2009 in der Disziplin Blitzöffnung, Michael Hünseler, gibt eine theoretische und praktische Einführung.
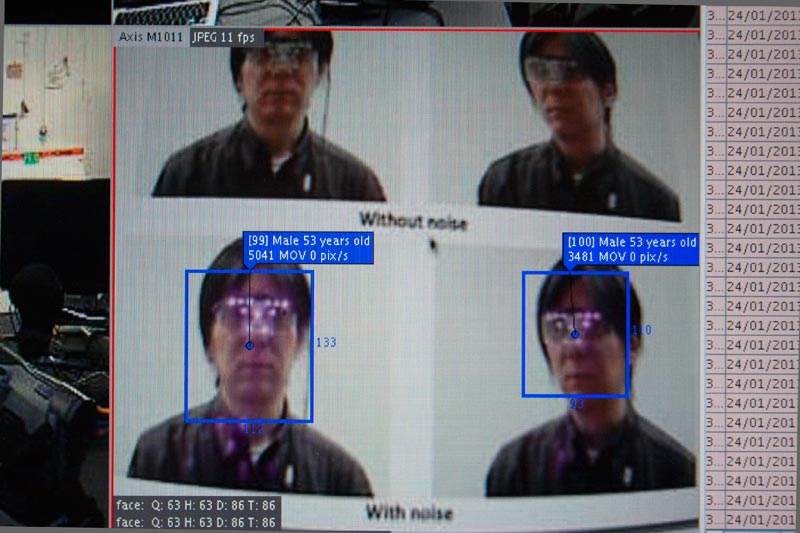
Im zweiten Teil beschäftigen wir uns mit den eingebauten Fehlern und Merkwürdigkeiten der von uns benutzten (meist elektronischen) Werkzeuge. Diese sollen kreativ neu interpretiert und gegen den vom Hersteller gedachten Zweck benutzt werden. Wir räumen den Geräteschrank des Surveillant Architectures Seminars aus, bringen alles zum Laufen, und bauen uns aus eigentlich nicht zusammen gehörenden Teilen neue vollautomatische Beobachtungs-Maschinen und live-Video Geräte.
Selten genutzte und oft gebrauchte Werkzeuge,
brandneue genauso wie veraltete Kameras,
schicke neue Formate und überholte, träge Protokolle,
Mac, PC, Linux, Smart- und not-so-smart Phones,
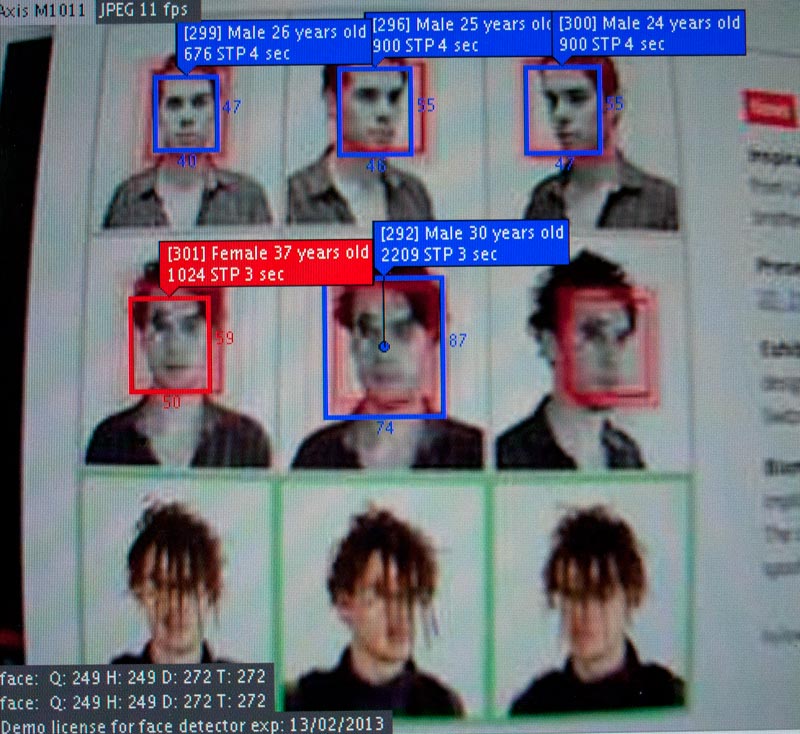
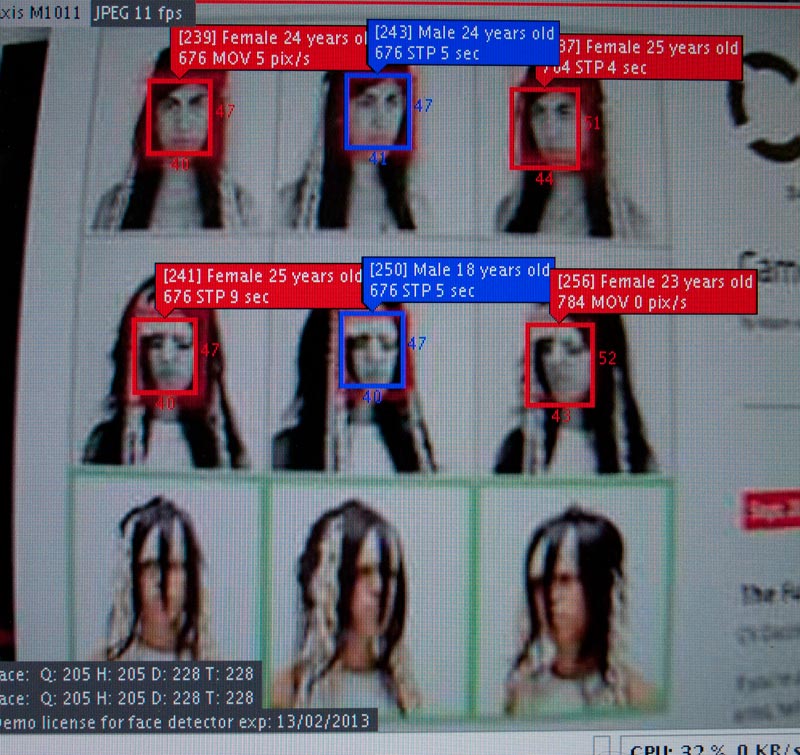
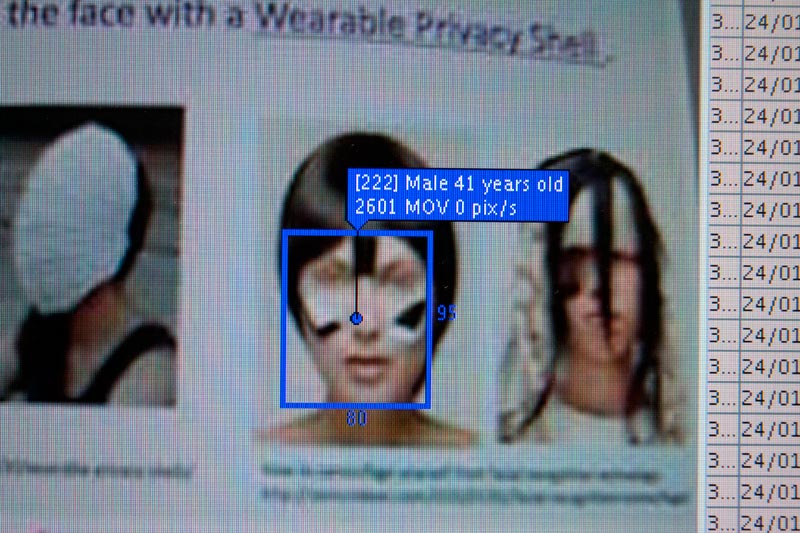
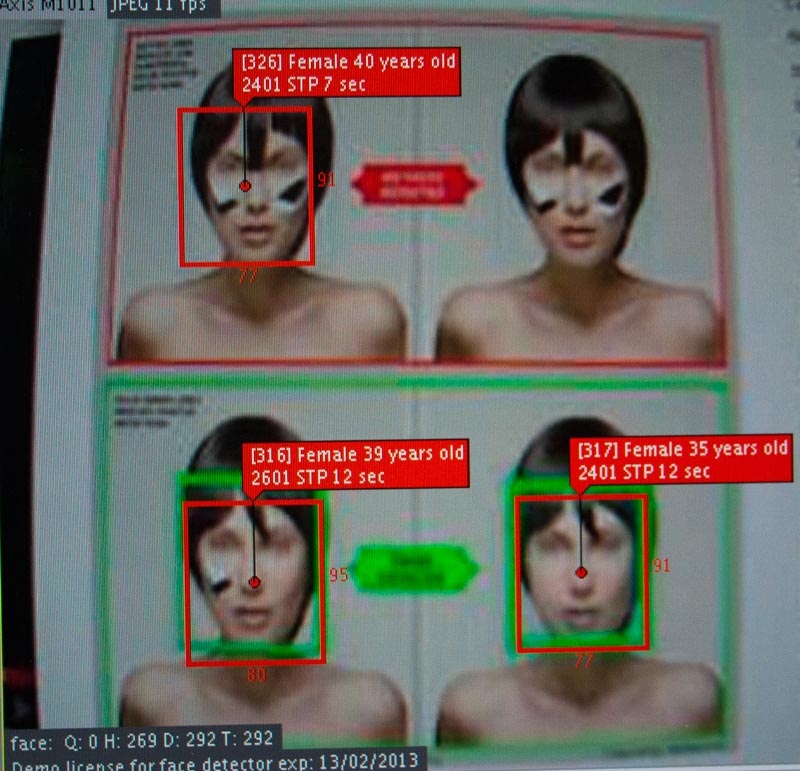
Sensoren und Trigger, Bewegungsmelder und Gesichtserkennung:
Aus allen diesen Gerätschaften sollen neue, bisher nicht bekannte Maschinen zusammengestöpselt werden – die uns vielleicht einmal später die Kunstarbeit abnehmen.
Bringt mit, was Ihr anschliessen wollt, wir finden einen Nutzen!
Aus organisatorischen Gründen ist die Teilnehmerzahl auf 10 begrenzt. Anmeldungen bitte an Christian sievers [at] khm [dot] de.
—
Wer sich einlesen möchte:
Literatur zum Lock Picking: http://www.ssdev.org/lockpicking/MIT_D/
Security Engineering, der Klassiker: http://www.cl.cam.ac.uk/~rja14/book.html (auch im Semesterapparat)